What are the 5 Major Types of Classic Security Models? - Cyber Security Certifications, Cyber Security Consulting, RogueLogics
![PDF] BTG-BIBA: A Flexibility-Enhanced Biba Model Using BTG Strategies for Operating System | Semantic Scholar PDF] BTG-BIBA: A Flexibility-Enhanced Biba Model Using BTG Strategies for Operating System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/83fcec720b425bbc4e764ff167afaea6721dbb3e/5-Figure3-1.png)
PDF] BTG-BIBA: A Flexibility-Enhanced Biba Model Using BTG Strategies for Operating System | Semantic Scholar
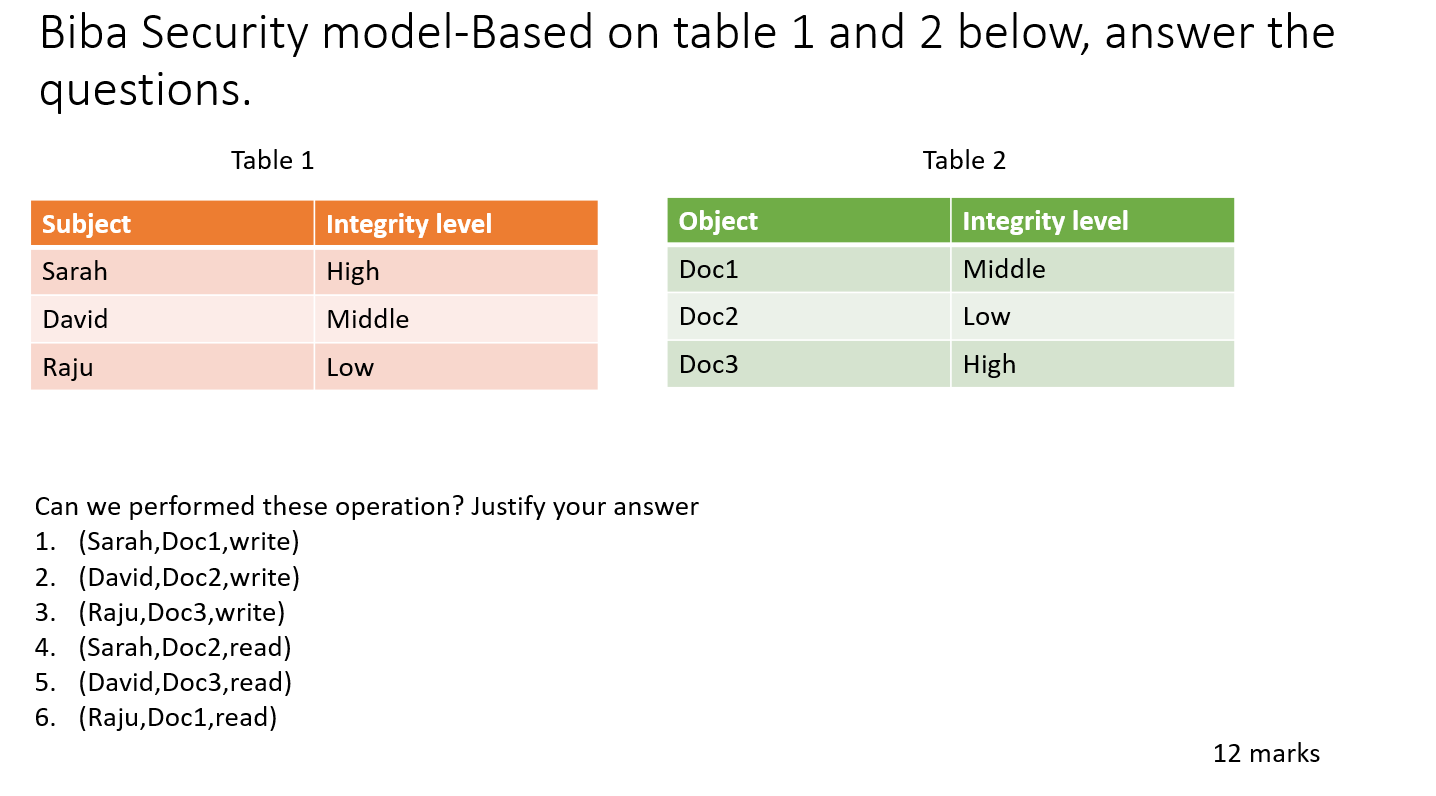
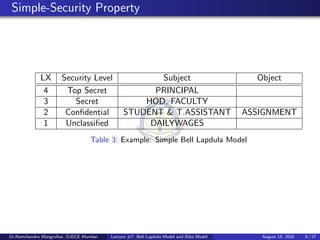
▻ Bell-LaPadula model ▻ Biba model ▻ Chinese Wall model ▻ (Clark-Wilson model) ▻ Demonstrate how security policies can

Generic metamodels for expressing configurations of (a) DAC; (b) BLP... | Download Scientific Diagram
![PDF] BTG-BIBA: A Flexibility-Enhanced Biba Model Using BTG Strategies for Operating System | Semantic Scholar PDF] BTG-BIBA: A Flexibility-Enhanced Biba Model Using BTG Strategies for Operating System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/83fcec720b425bbc4e764ff167afaea6721dbb3e/4-Figure2-1.png)